The threat to sensitive information’s integrity has continued to be tried by cyber-attacks, data breaches, and insider threats. In turn, most businesses have tried using advanced technologies to manage security. Among such security solutions, one of the most powerful is SIEM. A holistic approach to threat detection, real-time monitoring, and incident response offered by SIEM tools has made them crucial in modern security operations. In this article, we take a closer look at the benefits offered by SIEM solutions and what makes them irreplaceable in protecting an organization’s digital assets.
#1. Centralized Data Collection and Management
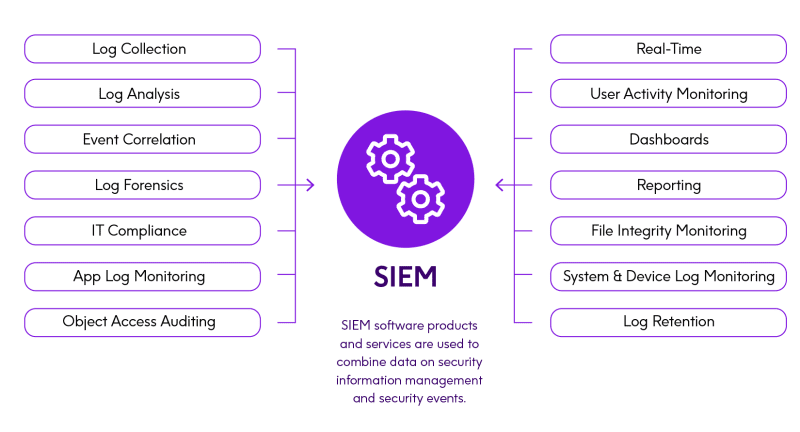
Image Source: Precisely
One of the major advantages of SIEM tools is that these utilities can collect security-related data from a wide array of sources, such as servers, firewalls, applications, network devices, and so on. Consolidating this data in one central platform enables an organization to examine its entire network. It eliminates the tedious process of manually collecting logs from disparate devices, hence enhancing efficiency and eliminating errors caused by human intervention.
Different SIEM tools utilize various mechanisms, such as log management, flow data collection, and endpoint data collection, to monitor and correlate security events. This provides a centralized approach that simplifies security operations and ensures that no important event is missed, hence giving total visibility into organizations’ security postures.
#2. Real-time Monitoring and Threat Detection
Every minute matters when it comes to cybersecurity. The consequences of a given danger are more severe the longer an organization takes to identify it and take appropriate action. SIEM systems provide real-time event monitoring linked to security. With the help of these solutions, organizations may shorten the average time it takes to recognize dangers and take action before they overwhelm them. SIEMs employ sophisticated correlation rules and algorithms to identify questionable patterns or unusual network activity.
Some examples include SIEM tools detecting unusual login attempts, spikes in network traffic, or unauthorized access to sensitive data. Once it identifies such anomalies, the system can automatically generate alerts and notifications of this to the security team.
#3. Advanced Threat Intelligence and Correlation
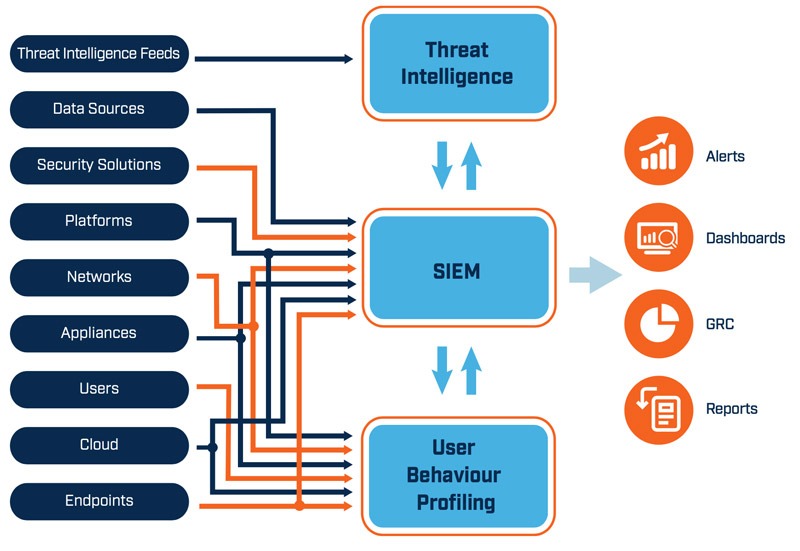
Image Source: Huntsmen
SIEM products improve their threat detection capabilities by integrating threat intelligence streams. These feeds include current information on known vulnerabilities, threats, and compromise indications. They can more successfully detect and rank possible security issues by integrating this threat knowledge into their analysis.
SIEM technologies can correlate security events with known attack patterns, signatures, and signs of compromise thanks to threat intelligence feeds. By promptly identifying and addressing any dangers, this proactive strategy assists businesses in staying one step ahead of hackers.
#4. Automated Response and Incident Management
Probably the greatest benefit derived from SIEM tools is the power to automate responses to certain types of security incidents. Organizations can configure in advance any actions that should be taken when specific threats are identified, such as blocking IP addresses, isolating compromised systems, or killing off hazardous user sessions.
It also includes speeding up the reaction to threats and reducing the workload for IT security teams. With the increasing number of cyberattacks, handling each one manually is too time-consuming and ineffective. Therefore, SIEM tools automate routine tasks for security personnel to redirect their forces to resolve an issue that requires human brains.
Third-party SIEM solutions allow for incident management by tracking security events throughout their life cycle, from detection to resolution. This enables the organization to track in detail what was done to handle incidents in general, adding accountability and post-incident analysis to its benefits.
#5. Compliance and Reporting
Another significant advantage of SIEM systems is their ability to assist a business in adhering to regulatory compliance regulations. Strict data protection and privacy regulations, including GDPR, HIPAA, and PCI-DSS, mandate that businesses maintain thorough records of security incidents and demonstrate their capacity for threat detection and response. These regulations affect a wide range of sectors.
SIEM solutions largely automate much of the compliance process by offering out-of-the-box reporting and template features aligned with regulatory frameworks. They also support the generation of audit trails and detailed reports on security incidents, user activity, and network access logs. This will not only ease the pain of compliance but also help organizations avoid costly penalties associated with non-compliance.
#6. Improved Incident Forensics and Root Cause Analysis
It is very important to know the ‘how’ of preventing a security breach in the future. Organizations looking into security issues might benefit from the forensic analysis capabilities offered by SIEM tools. SIEM solutions thereby come into play during incident forensics by supplying detailed timelines of security events. The detailed logs, combined with the search functionality of historical data, enable the security team to trace steps taken by cybercriminals to infiltrate the network.
Powerful search and analytics are core to SIEM systems, making pinpointing the actual root cause of an incident much easier for security professionals. Organizations can learn their vulnerabilities and how attackers utilize them, thus enabling them to take proactive measures to strengthen their defenses. These insights will also provide IT teams with more effective ways to build mitigations against future threats.
#7. Advanced Analytics
One essential component of contemporary SIEM tools is advanced analytics. These solutions use various methods, including behavior analytics and machine learning, to spot unusual activity and possible security breaches. By using sophisticated algorithms on security event data, SIEM products can identify irregularities and subtle trends that conventional security solutions can miss.
SIEM technologies with advanced analytics capabilities may create baselines of typical user, device, and application behavior. Any departure from these benchmarks may result in notifications that suggest possible security problems. SIEM solutions gradually increase the accuracy of their detections by continually learning from security incidents.
Conclusion
The increasing sophistication of cyber threats requires equally sophisticated tools to protect organizational data and networks. SIEM tools have emerged as a critical component in the modern era of cybersecurity, providing real-time monitoring, threat detection, workflow automation, and compliance support. Offering centralized visibility and enhancing incident response capabilities, the SIEM system supports an organization in outpacing dynamic threats with enhanced operational efficiency.

